Data Processing Addendum
(Last Updated: January 1, 2024)
When applicable, this Data Processing Addendum (“DPA”) and the 2021 Standard Contractual Clauses, along with its Schedules are incorporated into the Terms of Service Agreement or other written or electronic agreement (the “Agreement”) between Esker, Inc. (“Esker”) and Customer (collectively the “Parties”) for the purchase of the Esker On Demand Service (“the Service”) to reflect the Party’s agreement with regards to the Processing of Personal Data. By signing the Agreement, the Parties enter into this DPA and when applicable, the 2021 SCC. Customer, if applicable, enters into this DPA on behalf of itself and, to the extent required under applicable Data Protection Laws and Regulations, in the name and on behalf of its Authorized Affiliates. For the purposes of this DPA only, and except where indicated otherwise, the term "Customer" shall include Customer and Authorized Affiliates. This DPA will terminate automatically upon termination of the Agreement, or as terminated earlier pursuant to the terms of this DPA. In the course of providing the Service to the Customer pursuant to the Agreement, Esker may process Personal Data on behalf of Customer and the Parties agree to comply with the following provisions with respect to any Personal Data, each acting reasonably and in good faith. The duration of Processing will be the same as the duration of the Agreement, except as otherwise agreed in writing between the Parties. The scope and further details of the Processing activities to be performed by Esker under or in connection with the Agreement and this DPA which are attached herein.
1.0 Definitions. Unless otherwise defined in the Agreement, all capitalized terms used in this Addendum will have the meanings as given below:
1.1 “Affiliate” means any legal entity directly or indirectly controlling, controlled by, or under common control with a Party, where control means the ownership of a majority share of the stock, equity or voting interests of such entity.
1.2 “Authorized Affiliate” means any of Customer’s Affiliates which (a) are subject to the Data Protection Laws and Regulations, the European Economic Area and/or their member states, Switzerland and/or the United Kingdom, and (b) are permitted to use the Service pursuant to the Agreement between Customer and Esker, but has not signed its own Agreement with Esker and is not a “Customer” as defined in the Agreement.
1.3 “Controller” means the entity which determines the purposes and means of the Processing of Personal Data.
1.4 “Data Incident” means (a) any unlawful access to Personal Data stored in the Service or systems, equipment, or facilities of Esker, the Esker Entities, or its Sub-processors, or (b) unauthorized access to such the Service, systems, equipment, or facilities that results in loss, disclosure, or alteration of Personal Data.
1.5 “Data Protection Laws and Regulations” means (i) General Data Protection Regulation ("GDPR”); and (ii) any other data privacy or data protection laws or regulations of the European Union, the European Economic Area and their member states, the United Kingdom (UK) and Switzerland, that apply to the Processing of Personal Data under this DPA using the EU-U.S. Data Privacy Framework (EU-U.S. DPF), the UK Extension to the EU-U.S. Data Privacy Framework (UK Extension to the EU-U.S. DPF), or the Swiss-U.S. Data Privacy Framework (Swiss-U.S. DPF) as a recognized acceptable transfer mechanism.
1.6 “Data Subject” means the identified or identifiable person to whom Personal Data relates.
1.7 “Esker Entities” means Esker’s parent company, Esker, S.A., and any of its affiliates.
1.8 “Frameworks” means the EU-U.S. Data Privacy Framework (EU-U.S. DPF), the UK Extension to the EU-U.S. Data Privacy Framework (UK Extension to the EU-U.S. DPF), and the Swiss-U.S. Data Privacy Framework (Swiss-U.S. DPF) were respectively developed in furtherance of transatlantic commerce by the U.S. Department of Commerce and the European Commission, the UK Government, and the Swiss Federal Administration to provide U.S. organizations with reliable mechanisms for Personal Data transfers to the United States from the European Union / European Economic Area, the United Kingdom (and Gibraltar), and Switzerland while ensuring data protection that is consistent with EU, UK, and Swiss law.
1.9 “GDPR” means the EU General Data Protection Regulation (GDPR) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the Processing of Personal Data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation), OJ 2016 L 119/1.
1.10 “GDPR” means the EU General Data Protection Regulation (“GDPR”) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the Processing of Personal Data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation), OJ 2016 L 119/1.
1.11 “Personal Data” means any information that is uploaded to the Service under Customer’s account or that is otherwise disclosed to Esker by Customer when using the Service that relates to (i) an identified or identifiable natural person and, (ii) an identified or identifiable legal entity (where such information is protected similarly as Personal Data or personally identifiable information under applicable Data Protection Laws and Regulations), where for each (i) or (ii) such data is Personal Data.
1.12 “Processing” means any operation or set of operations which is performed upon Personal Data, whether or not by automatic means, such as collection, recording, organization, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction, erasure or destruction.
1.13 “Processor” means the entity which processes Personal Data on behalf of the Controller.
1.14 “Sensitive Personal Data” means Personal Data revealing racial or ethnic origin, political opinions, religious or philosophical beliefs, or trade union membership, and the Processing of genetic data, biometric data for the purpose of uniquely identifying a natural person, data concerning health or data concerning a natural person’s sex life or sexual orientation. Sensitive Personal Data shall also include genetic data, biometric data, and data concerning health as defined in GDPR Article 4 (13), (14), and (15).
1.15 “Standard Contractual Clauses (“2021 SCC”)” means the standard contractual clauses adopted by Commission Implementing Decision (EU) 2021/914 of 4 June 2021 on standard contractual clauses for the transfer of Personal Data to third countries pursuant to Regulation (EU) 2016/679 of the European Parliament and of the Council as currently set out at https://eur-lex.europa.eu/eli/dec_impl/2021/914/oj.
1.16 “United Kingdom Standard Contractual Clauses Addendum” shall mean, when applicable, the International Data Transfer Addendum to the EU Commission Standard Contractual Clauses (“UK Addendum”) as specified by the Information Commissioner’s Office (ICO) of the United Kingdom and set forth at the ICO’s website from time to time at available on the ICO’s website at https://ico.org.uk/for-organisations/guide-to-data-protection/guide-to-the-general-data-protection-regulation-gdpr/international-data-transfer-agreement-and-guidance/ as supplemented by the International Data Transfer Addendum to the EU Commission Standard Contractual Clauses attached hereto as Schedule 3.
1.17 “Sub-Processors” means (a) all Esker Entities that have access to, and process, Personal Data, and (b) all third parties (other than Esker Entities) that are contractually engaged by Esker to provide services to Customer and that have access to, and process, Personal Data.
2.0 Data Processing.
2.1 Roles of the Parties. The Parties acknowledge and agree that with regard to the Processing of Personal Data, Customer is the Controller, Esker is the Processor, and that Esker will engage Sub-Processors pursuant to the requirements set forth elsewhere in this DPA. Esker will not process Personal Data, except as necessary to provide the Service. Customer shall at all times during this DPA comply with all its obligations as a Controller under the applicable Data Protection Laws and Regulations. Esker shall at all times during this DPA comply with all its obligations as a Processor under the applicable Data Protection Laws and Regulations. Furthermore, Esker will process Personal Data in accordance with the Data Protection Laws and Regulations directly applicable to Esker’s provisioning of the Service. Upon Customer’s written request, Esker will provide Customer with reasonable cooperation and assistance needed for Customer to fulfill its obligations under the Data Protection Laws and Regulations: (i) to carry out a data protection impact assessment related to Customer’s use of the Service, to the extent Customer does not otherwise have access to the relevant information, and to the extent such information is available to Esker, (ii) in consultations with the supervisory authority prior to Processing where a data protection impact assessment indicates that the Processing would result in a high risk in the absence of measures taken by the Controller to mitigate the risk, and (iii) in responding to a Data Incident. Customer shall remain solely responsible and liable for complying with any data protection assessment obligation under applicable Data Protection Laws and Regulations. As part of providing the Service, Esker may collect, use, and disclose quantitative data derived from the use of the Service by the Customer for service improvements, industry analysis, benchmarking, analytics and supporting Customer's usage of the Service. All data disclosed will be in aggregate and anonymous form only and will not identify Customer or its specific users or its relationship to their suppliers.
2.2 Customer’s Instructions for Data Processing. Esker will process Personal Data in accordance with Customer’s instructions. Esker will treat all Personal Data as Confidential Information as defined in the Agreement. The Parties agree that the Agreement and this DPA is Customer’s complete and final instructions to Esker in relation to Processing of Personal Data. Processing outside the scope of this DPA, if any, unless required to do so by Data Protection Laws and Regulations to which Esker is subject, will require prior written agreement between Esker and Customer on additional instructions for Processing, including agreement on any additional fees Customer will pay to Esker for carrying out such instructions. All of Customer’s instructions shall comply with the Data Protection Laws and Regulations. Customer may terminate this DPA if Esker declines to follow instructions requested by Customer that are outside the scope of this DPA.
2.3 Customers Processing of Personal Data. Customer shall, in its use of the Service, process Personal Data in accordance with the requirements of Data Protection Laws and Regulations. Customer’s instructions for the Processing of Personal Data shall comply with Data Protection Laws and Regulations. Customer shall have responsibility for the accuracy, quality, and legality of Personal Data provided by Customer to Esker and the means by which Customer acquired such Personal Data, provided that Esker shall immediately inform the Customer if, in its opinion, an instruction infringes the applicable Data Protection Laws and Regulations.
2.4 Personnel. Esker shall ensure that its personnel engaged in the Processing of Personal Data are informed of the confidential nature of the Personal Data, have received appropriate training on their responsibilities and are subject to obligations of confidentiality at least as restrictive as the Agreement and this DPA, and that such obligations shall survive the termination of that person’s engagement with Esker. Esker shall take commercially reasonable steps to ensure the reliability of any Esker personnel engaged in the Processing of Personal Data. Esker shall ensure that access to Personal Data is limited to those personnel performing services in accordance with the Agreement and that its personnel Process the minimum amount of Personal Data needed to provide the Services in accordance with this Agreement.
2.5 Data Subject Rights. Esker shall ensure that its personnel engaged in the Processing of Personal Data are informed of the confidential nature of the Personal Data, have received appropriate training on their responsibilities and are subject to obligations of confidentiality at least as restrictive as the Agreement and this DPA, and that such obligations shall survive the termination of that person’s engagement with Esker. Esker shall take commercially reasonable steps to ensure the reliability of any Esker personnel engaged in the Processing of Personal Data. Esker shall ensure that access to Personal Data is limited to those personnel performing services in accordance with the Agreement and that its personnel Process the minimum amount of Personal Data needed to provide the Services in accordance with this Agreement.
2.6 Legally Required Disclosures. If Esker receives any subpoena, judicial, administrative, or arbitral order of an executive or administrative agency, regulatory agency, or other governmental authority which is related to the Personal Data (“Disclosure Request”), it will promptly pass on such Disclosure Request to Customer without responding to it, unless otherwise required by applicable law (including to provide an acknowledgement of receipt to the authority that made the Disclosure Request).
2.7 Return and Deletion of Personal Data. Personal Data shall only be retained for as long as it is necessary to perform the Services as specified in the Agreement and shall be returned to Customer or deleted upon termination of the Agreement. In the event the Agreement is terminated for any reason, archived Documents shall be made available to Customer until the end of any archive commitment period.
3.0 Security. Esker has implemented and shall maintain appropriate technical and organizational measures for the Processing of Personal Data. These measures take into account the nature, scope, and purposes of Processing as specified in this DPA, and are intended to protect Personal Data against the risks inherent to the Processing of Personal Data in the performance of the Service, in particular risks from accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to Personal Data transmitted, stored, or otherwise processed. In particular, Esker has implemented appropriate physical access, system access, data access, transmission and encryption, input, data backup, and security oversight, enforcement, and other security controls and measures which are set forth in Schedule 2 herein.
4.0 Personal Data Transfer Mechanisms. Esker complies with and relies on the Frameworks regarding the collection, use, and retention of Personal Data transferred from the European Union, and Switzerland, as applicable, to the United States in reliance on the Data Privacy Framework. Esker has certified to the Department of Commerce that it adheres to the Data Privacy Framework Principles with respect to such data. If there is any conflict between the terms in this notice and the Frameworks, the Frameworks shall govern. In the event one of the Frameworks is invalidated, the 2021 SCC, as defined herein and modified as set forth in Schedule 1, shall apply to Personal Data that is transferred outside the European Economic Area (“EEA”), either directly or via onward transfer, to any country not recognized by the European Commission as providing an adequate level of protection for Personal Data (as described and defined in the GDPR). The 2021 SCC shall not apply to Personal Data that is not transferred, either directly or via onward transfer, outside the EEA. Additionally, Personal Data in the Service will be hosted in regional data centers. Esker will not migrate Customer’s Personal Data to a different regional data center without Customer’s prior written authorization except as necessary to comply with the law or a valid and binding order of a law enforcement agency. To date, Esker has received no Section 702 FISA or EO 12333 requests from any United States Federal Government entity. Notwithstanding the previous sentence, in accordance with the Data Protection Laws and Regulations Esker may access and process Personal Data on a global basis as necessary to perform the Service, as well as for purposes such as: IT security, maintenance and performance and related infrastructure, and technical and professional services support.
5.0 Third-Party Certifications. Esker is certified under ISO 27001 and agrees to maintain an information security program for the Esker on Demand and FlyDoc Products that complies with the ISO 27001 standards or such other alternative standards as are substantially equivalent to ISO 27001 for the establishment, implementation, control, and improvement of the Esker security standards. Esker uses external third-party auditors to verify the adequacy of its security measures, including the security of the physical data centers. This audit: (a) will be performed at least annually; (b) will be performed according to ISO 27001 standards or such other alternative standards that are substantially equivalent to ISO 27001; and (c) will be performed by independent third-party security professionals at Esker’s selection and expense. Upon Customer’s written request, and subject to the confidentiality obligations set forth in the Agreement or a non-disclosure agreement, Esker shall provide Customer with a copy of Esker’s most recent third-party audits reports or certifications, as applicable. Customer is solely responsible for reviewing the information made available by Esker relating to data security and making an independent determination as to whether the Service meets Customer’s requirements and for ensuring that Customer’s personnel and consultants follow the guidelines they are provided regarding data security.
6.0 Auditing Rights. On at least an annual basis, or as otherwise requested in writing by a Customer, Esker shall make available copies of its SSAE-18 SOC1 Type II, or current equivalent, audit report for examination of Esker’s internal controls and procedure with regard to Services, deliverables, professional services, work product and work provided under the Agreement. In addition, in connection with the audit rights granted to Customer under the Agreement, during the term of the Agreement and for a period of one year thereafter, Customer has the right to audit Esker, once a year, by following the steps here below and according to the following conditions: Step 1: Per Customer’s written request, Esker will supply a copy of audit reports related to the current certifications in place within Esker or other materials to ensure Esker’s compliance with the terms of the Agreement for Customer and/or its independent auditor’s remote review and consideration; Step 2: if Customer’s audit key points are not covered by those reports or there are any reasonable concerns with the completeness or veracity of those reports, Customer or an independent auditor appointed by Customer, will be able to send a second written request to supplement or clarify the responses provided under Step 1 for Customer and/or its independent auditor’s remote review and consideration; Step 3: If there are any questions regarding the completeness or veracity of the information provided under Step 2, Customer or its auditor may organize a conference call with the Esker representatives subject to reasonable prior notice and a detailed agenda. At no time during any audit shall Customer, any of its employees, or any third party acting on behalf of the Customer be permitted to conduct its own physical testing of any kind, be it remote, on premise, or over-the-shoulder testing, of any part of the Esker on Demand Technical Platform. Unless the audit is mandated by a regulatory or a judicial authority, any audit request shall be subject to the above procedure only. The Esker on Demand Technical Platform are defined as a group of infrastructures, composed of software and hardware and designed to run the specific Esker on Demand Product.
7.0 Breach Notification. Esker will notify Customer of a Data Incident in accordance with the requirements specified in GPDR Article 33 (2) after Esker becomes aware of such Data Incident and takes reasonable steps to identify the cause, mitigate the effects and minimize any damage resulting from a Data Incident. Customer agrees that an unsuccessful Data Incident will not be subject to this section. An unsuccessful Data Incident is one that results in no unauthorized access to Personal Data or to any of Esker’s equipment or facilities storing Personal Data, and may include, without limitation, pings and other broadcast attacks on firewalls or edge servers, port scans, unsuccessful log-on attempts, denial of service attacks, packet sniffing (or other unauthorized access to traffic data that does not result in access beyond IP addresses or headers) or similar incidents; and Esker’s obligation to report or respond to a Data Incident under this section is not and will not be construed as an acknowledgement by Esker of any fault or liability of Esker with respect to a Data Incident. Notifications of Data Incidents, if any, will be delivered to one or more of Customer’s administrators by any means Esker selects, including via e-mail. It is Customer’s sole responsibility to ensure Customer’s administrators maintain accurate contact information with Esker to ensure proper notification. The obligations herein shall not apply to Data Incidents that are caused by Customer or Customer’s users and shall, in no way, have any bearing on Customer’s communication obligations to Data Subjects as specified under the law.
8.0 Esker Entities and Sub-processors. Customer agrees and consents to Esker using Esker Entities and Sub-Processors to fulfill its contractual obligations under this DPA or to provide certain services to Customer on its behalf, such as professional services, technical support services, and telecommunication services. Esker maintains a list of authorized Sub-Processors, which is available to Customer for review upon written request. Within ten (10) business days of Esker notifying Customer that an Esker Entity or Sub-Processors would be providing certain services, Customer may object to the intended involvement in writing to Esker. In the event Customer’s objection is justified, Esker and Customer will work together in good faith to find a mutually acceptable resolution to address such objection. To the extent Esker and Customer are unable to reach a mutually acceptable resolution within a reasonable time frame, Customer shall have the right to terminate the Agreement in accordance with its terms. Esker will restrict the Esker Entities and Sub-Processors’ access to Personal Data to only what is necessary to perform the Service or to provide the Service to Customer and any of Customer’s users in accordance with the documentation provided by Esker and Esker will prohibit the Esker Entities or Sub-Processors from accessing Personal Data for any other purpose. Esker will impose appropriate contractual obligations in writing upon the Esker Entities or Sub-Processors that are no less protective than this DPA, including relevant contractual obligations regarding confidentiality, data protection, data security, and audit rights. Esker will remain responsible for the performance of the Esker Entities and Sub-Processors’ obligations in compliance with the terms of this DPA and Data Protection Laws and Regulations.
9.0 Nondisclosure. Customer agrees that the details of this DPA are not publicly known and constitute each Party’s Confidential Information under the confidentiality provisions of the Agreement or non-disclosure agreement. If the Agreement does not include a confidentiality provision protecting Esker’s confidential information and Customer and Esker, or the Esker Entities, do not have a non-disclosure agreement in place covering this DPA, then Customer shall not disclose the contents of this DPA to any third party except as required by applicable law.
10.0 Global Data Protection Officer; Chief Compliance Officer-United States. Esker’s Global Data Protection Officer can be contacted at euprivacy@esker.com. Esker’s Chief Compliance Officer in the United States can be contacted at usprivacy@esker.com
11.0 Entire Agreement; Conflict. Except as amended by this DPA and the Schedules attached hereto, the Agreement will remain in full force and effect. If there is a conflict between the Agreement and this DPA, the terms of this DPA will control solely as to the subject matter contained herein. In all other instances, the Agreement shall govern. When necessary, the relevant provisions contained in the 2021 SCC are hereby incorporated by reference and are an integral part of this DPA. Any clauses that require specific modules or optional language as provided by the EU Commission for the purposes of a complete 2021 SCC are set out in Schedule 1. The information required for the purposes of the Appendices to the 2021 SCC are set out in Schedule 2. If, at any time the Data Protection Laws or Regulations require any further steps to be taken in order to permit the transfer of Personal Data as envisaged under this DPA, then Customer and Esker shall work together in good faith to take all steps reasonably required to ensure that the transfer of Personal Data meets the requirements of Data Protection Laws and Regulations. This DPA may be executed in one or more counterparts, each of which shall be deemed an original, but all of which together shall constitute one and the same instrument. Both parties have read, understand, and agree to the terms of this DPA.
SCHEDULE 1: STANDARD CONTRACTUAL CLAUSES OPERATIVE PROVISIONS AND ADDITIONAL TERMS
Module 2 (Controller to Processor) shall apply as follows: Clause 7 (Docking Clause): Parenthetical (a) shall apply; and regarding Clause 17 the Parties agree the Member State shall be France and the Choice of forum and jurisdiction in Clause 18 shall be the courts of Lyon, France.
Additionally, the General Written Authorisation for Module 2 shall apply to Clause 9 (Use of Sub-Processors) with further information described in Schedule 2. Further details of Clause 13 are described in Schedule 2.
SCHEDULE 2: DESCRIPTION OF PROCESSING/TRANSFER
LIST OF PARTIES
Data exporter(s):
Name: The entity identified as “Customer” in the introductory paragraph of the Agreement.
Address: Customer’s address as specified in the introductory paragraph of the Agreement.
Contact person’s name, position and contact details: Customer’s contact information is specified in the Agreement.
Activities relevant to the data transferred under these Clauses: The activities as specified in various Exhibits of the Agreement.
Signature and date: By signing the Agreement, the data exporter will be deemed to have signed this Schedule.
Role: Controller
Data importer(s):
Name: Esker, Inc.
Address: 1850 Deming Way, Ste. 150, Middleton, WI 53562
Contact person’s name, position and contact details: The contact details for Esker’s Global Data Protection Officer are specified in the DPA.
Activities relevant to the data transferred under these Clauses: The activities as specified in various Exhibits of the Agreement.
Signature and date: By signing the Agreement, the data importer will be deemed to have signed this Schedule.
Role: Processor
DESCRIPTION OF TRANSFER
Categories of Data Subjects whose personal data is transferred: Customer may submit Personal Data to the Service, the extent of which is determined and controlled by Customer in its sole discretion, and which may include, but is not limited to Personal Data relating to the following categories of Data Subjects:
● Prospects, customers, business partners and vendors of Customer (who are natural persons)
● Employees or contact persons of Customer’s prospects, customers, business partners and vendors
● Employees, agents, advisors, freelancers of Customer (who are natural persons)
● Customer’s Users authorized by Customer to use the Services
Categories of personal data transferred: Customer may submit Personal Data to the Service, the extent of which is determined and controlled by Customer in its sole discretion, and which may include, but is not limited to the following categories of Personal Data:
● First and last name
● Title and Position
● Employer
● Contact information (company, email, phone, physical business address)
● Log-in credentials
● Professional life data
● Connection data (including ERP information)
● Purchasing data
Sensitive Data transferred (if applicable) and applied restrictions or safeguards that fully take into consideration the nature of the data and the risks involved, such as for instance strict purpose limitation, access restrictions (including access only for staff having followed specialized training), keeping a record of access to the data, restrictions for onward transfers or additional security measures: Data exporter may submit special categories of data to the Service, the extent of which is determined and controlled by the data exporter in its sole discretion, and which is for the sake of clarity Personal Data with information revealing racial or ethnic origin, political opinions, religious or philosophical beliefs, or trade-union membership, and the Processing of genetic data, biometric data for the purpose of uniquely identifying a natural person, data concerning health or data concerning a natural person’s sex life or sexual orientation. Sensitive Data benefits from the same level of security as other categories of data within the Service.
The frequency of the transfer (e.g. whether the data is transferred on a one-off or continuous basis): On a continuous basis for the duration as defined in the Agreement.
Nature of the Processing: Collect, record, organize, structure, store, adapt or alter, retrieve, consult, use, disclose by transmission, disseminate or otherwise make available, align or combine, restrict, erase or destruct.
Purpose(s) of the data transfer and further Processing: Esker will Process Personal Data as necessary to perform the Service pursuent to the Agreement.
The period for which the personal data will be retained, or, if that is not possible, the criteria used to determine that period: The duration of the personal data process is defined in the Agreement and in any applicable Esker Privacy Policy.
For transfers to (sub-) processors, also specify subject matter, nature and duration of the Processing: As described below.
COMPETENT SUPERVISORY AUTHORITY
Competent supervisory authority/ies in accordance with Clause 13:
● Where the data exporter is established in an EU Member State: The supervisory authority with responsibility for ensuring compliance by the data exporter with Regulation (EU) 2016/679 as regards the data transfer shall act as competent supervisory authority.
● Where the data exporter is not established in an EU Member State, but falls within the territorial scope of application of Regulation (EU) 2016/679 in accordance with its Article 3(2) and has appointed a representative pursuant to Article 27(1) of Regulation (EU) 2016/679: The supervisory authority of the Member State in which the representative within the meaning of Article 27(1) of Regulation (EU) 2016/679 is established shall act as the competent supervisory authority.
● Where the data exporter is not established in an EU Member State, but falls within the territorial scope of application of Regulation (EU) 2016/679 in accordance with its Article 3(2) without however having to appoint a representative pursuant to Article 27(2) of Regulation (EU) 2016/679: Commission nationale de l'informatique et des libertés (CNIL) - 3 Place de Fontenoy, 75007 Paris, France shall act as the competent supervisory authority.
● Where the data exporter is established in the United Kingdom or falls within the territorial scope of application of UK Data Protection Laws and Regulations, the Information Commissioner's Office shall act as the competent supervisory authority.
● Where the data exporter is established in Switzerland or falls within the territorial scope of application of Swiss Data Protection Laws and Regulations, the Swiss Federal Data Protection and Information Commissioner shall act as competent supervisory authority insofar as the relevant data transfer is governed by Swiss Data Protection Laws and Regulations.
TECHNICAL AND ORGANISATIONAL MEASURES INCLUDING TECHNICAL AND ORGANISATIONAL MEASURES TO ENSURE THE SECURITY OF THE DATA
The data importer represents that it has adopted and implemented technical and organizational measures to protect Personal Data against accidental, unauthorized or unlawful destruction, loss, alteration, disclosure, and access, and against all other unlawful activities. To fulfill its obligations under this section, the data importer shall have in place, at a minimum any physical, technical, administrative, and organizational safeguards that provide for and ensure: (a) protection of business facilities, paper files, servers, computing equipment with information storage capabilities; and backup systems containing Personal Data; (b) network, application (including databases) and platform security; (c) business systems designed to optimize security and proper disposal of Personal Data according to the terms of these Clauses; (d) secure transmission and storage of personal information; (e) authentication and access control mechanisms over personal information, media, applications, operating systems and equipment; (f) personnel security and integrity, including background checks where consistent with applicable law; (g) annual training to the data importer’s employees on how to comply with the data importer’s physical, technical, and administrative information security safeguards and confidentiality obligations under applicable laws, rules, regulations and guidelines; and (h) storage limitations such that Personal Data resides only on servers in data centers that comply with industry standard data centers that have security controls. Data Importer will not materially decrease the overall security of the Service during a subscription term.
The data importer uses external auditors to verify the adequacy of its security measures, including the security of the physical data centers from which the Data importer provides services. This audit: (a) will be performed at least annually; (b) will be performed according to SSAE18/ISAE3402 or ISO 27001 standards or such other alternative standards that are substantially equivalent to SSAE18/ISAE3402 or ISO 27001; (c) will be performed by independent third-party security professionals at the data importer’s selection and expense; and (d) will result in the generation of a confidential audit report.
LIST OF SUB-PROCESSORS
The controller has authorized the use of the following sub-processors:
1. CDW – USA
Description of Processing: Physical and environmental security, managed internet access, and housing facility services.
Specific technical and organizational measures to be taken by the (sub-) processor to be able to provide assistance to the controller and, for transfers from a processor to a sub-processor, to the data exporter:
Esker monitors CDW for technical and organizational measures using documentary audit. On an annual basis, Esker request the latest available audit reports conducted for CDW (SOC 2 Type II). Esker verifies that the examination does not mention abnormal remaining exceptions in a section related to “Management Response to Exceptions” This confirms that CDW maintains its conformity.
2. Microsoft Azure – USA & Canada
Description of Processing: Physical and environmental security, managed Internet access, Infrastructure as a Service (IAAS), and Software as a Service (SAAS).
Specific technical and organizational measures to be taken by the (sub-) processor to be able to provide assistance to the controller and, for transfers from a processor to a sub-processor, to the data exporter:
Esker monitors Microsoft Azure and Azure Services for technical and organizational measures using documentary audit. Esker request the latest available audit reports conducted for Microsoft Azure Service (SOC 1 type II, SOC 2 Type II, ISO 27001). Esker verifies that the examination does not mention abnormal remaining exceptions in a section related to “Management Response to Exceptions” This confirms that Microsoft Azure maintains its conformity.
3. Amazon Web Service (AWS) – USA
Description of Processing: Physical and environmental security, managed Internet access, Infrastructure as a Service (IAAS), and Software as a Service (SAAS).
Specific technical and organizational measures to be taken by the SubPprocessor to be able to provide assistance to the Controller and, for transfers from a Processor to a Sub-Processor, to the data exporter:
Esker monitors Amazon Web Service for technical and organizational measures using documentary audit. Esker request the latest available audit reports conducted for AWS (SOC 1 type II, SOC 2 Type II, ISO 27001). Esker verifies that the examination does not mention abnormal remaining exceptions in a section related to “Management Response to Exceptions” This confirms that AWS maintains its conformity.
4. Esker S.A. – France
Description of Processing: Upon Customer request, Esker S.A. may provide professional service, technical support, and/or customer service services to Customer’s of Esker Inc.
Specific technical and organizational measures to be taken by the Sub-Processor to be able to provide assistance to the Controller and, for transfers from a Processor to a Sub-Processor, to the data exporter:
Esker is a subsidiary of Esker S.A. and provides Esker Inc. with necessary security audit reports. Esker verifies that the examination does not mention abnormal remaining exceptions in a section related to “Management Response to Exceptions” This confirms that Esker S.A. maintains its conformity.
5. Market Dojo – United Kingdom
Description of Processing: Upon Customer request, Market Dojo may provide professional service, technical support, and/or customer service services to the Market Dojo sourcing business solution.
Specific technical and organizational measures to be taken by the Sub-Processor to be able to provide assistance to the Controller and, for transfers from a Processor to a Sub-Processor, to the data exporter:
Market Dojo is a subsidiary of Esker and provides Esker with necessary security audit reports. Esker verifies that the examination does not mention abnormal remaining exceptions in a section related to “Management Response to Exceptions” This confirms that Market Dojo maintains its conformity.
SCHEDULE 3: UK ADDENDUM
Standard Data Protection Clauses to be issued by the Commissioner under S119A(1) Data Protection Act 2018
International Data Transfer Addendum to the EU Commission Standard Contractual Clauses
VERSION B1.0, in force 21 March 2022
This Addendum has been issued by the Information Commissioner for Parties making Restricted Transfers. The Information Commissioner considers that it provides Appropriate Safeguards for Restricted Transfers when it is entered into as a legally binding contract.
Part 1: Tables
Table 1: Parties
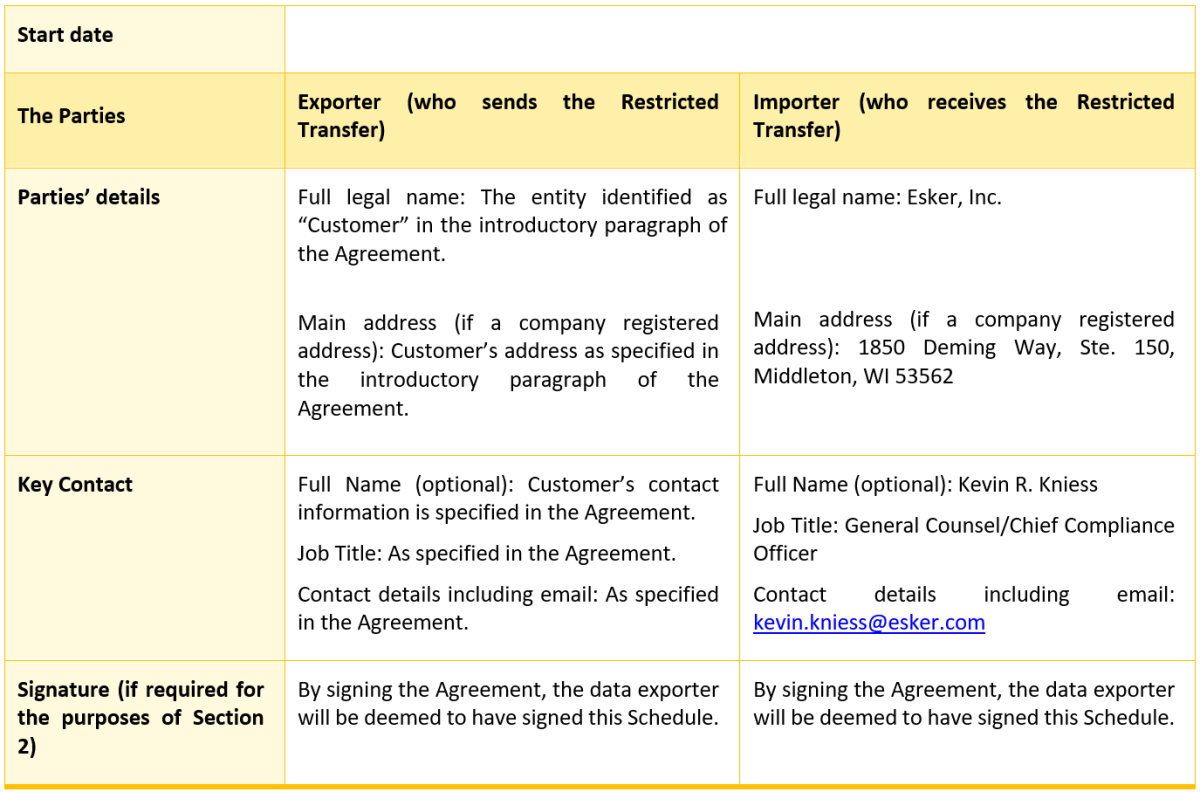
Table 2: Selected SCCs, Modules, and Selected Clauses
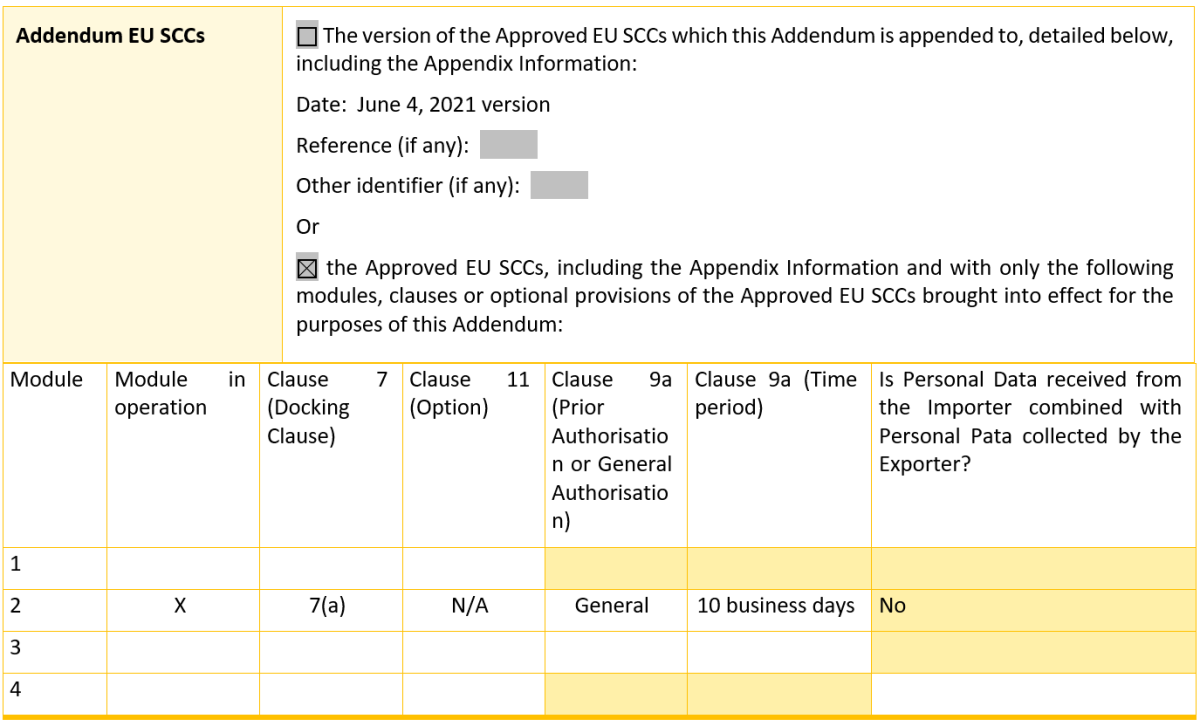
Table 3: Appendix Information
“Appendix Information” means the information which must be provided for the selected modules as set out in the Appendix of the Approved EU SCCs (other than the Parties), and which for this Addendum is set out in:
Annex 1A: List of Parties: As described in Schedule 2 of the DPA.
Annex 1B: Description of Transfer: As described in Schedule 2 of the DPA.
Annex II: Technical and organisational measures including technical and organisational measures to ensure the security of the data: As described in Schedule 2 of the DPA.
Annex III: List of Sub-Processors (Modules 2 and 3 only): As described in Schedule 2 of the DPA.
Table 4: Ending this Addendum when the Approved Addendum Changes

Part 2: Mandatory Clauses
Entering into this Addendum
Each Party agrees to be bound by the terms and conditions set out in this Addendum, in exchange for the other Party also agreeing to be bound by this Addendum.
Although Annex 1A and Clause 7 of the Approved EU SCCs require signature by the Parties, for the purpose of making Restricted Transfers, the Parties may enter into this Addendum in any way that makes them legally binding on the Parties and allows Data Subjects to enforce their rights as set out in this Addendum. Entering into this Addendum will have the same effect as signing the Approved EU SCCs and any part of the Approved EU SCCs.
Interpretation of this Addendum
Where this Addendum uses terms that are defined in the Approved EU SCCs those terms shall have the same meaning as in the Approved EU SCCs. In addition, the following terms have the following meanings:
This Addendum must always be interpreted in a manner that is consistent with UK Data Protection Laws and so that it fulfils the Parties’ obligation to provide the Appropriate Safeguards.
If the provisions included in the Addendum EU SCCs amend the Approved SCCs in any way which is not permitted under the Approved EU SCCs or the Approved Addendum, such amendment(s) will not be incorporated in this Addendum and the equivalent provision of the Approved EU SCCs will take their place.
If there is any inconsistency or conflict between UK Data Protection Laws and this Addendum, UK Data Protection Laws applies.
If the meaning of this Addendum is unclear or there is more than one meaning, the meaning which most closely aligns with UK Data Protection Laws applies.
Any references to legislation (or specific provisions of legislation) means that legislation (or specific provision) as it may change over time. This includes where that legislation (or specific provision) has been consolidated, re-enacted and/or replaced after this Addendum has been entered into.
Hierarchy
Although Clause 5 of the Approved EU SCCs sets out that the Approved EU SCCs prevail over all related agreements between the parties, the parties agree that, for Restricted Transfers, the hierarchy in Section 10 will prevail.
Where there is any inconsistency or conflict between the Approved Addendum and the Addendum EU SCCs (as applicable), the Approved Addendum overrides the Addendum EU SCCs, except where (and in so far as) the inconsistent or conflicting terms of the Addendum EU SCCs provides greater protection for Data Subjects, in which case those terms will override the Approved Addendum.
Where this Addendum incorporates Addendum EU SCCs which have been entered into to protect transfers subject to the General Data Protection Regulation (EU) 2016/679 then the Parties acknowledge that nothing in this Addendum impacts those Addendum EU SCCs.
Incorporation of and changes to the EU SCCs
This Addendum incorporates the Addendum EU SCCs which are amended to the extent necessary so that:
a) together they operate for data transfers made by the data exporter to the data importer, to the extent that UK Data Protection Laws apply to the data exporter’s Processing when making that data transfer, and they provide Appropriate Safeguards for those data transfers;
b)Sections 9 to 11 override Clause 5 (Hierarchy) of the Addendum EU SCCs; and
c) this Addendum (including the Addendum EU SCCs incorporated into it) is (1) governed by the laws of England and Wales and (2) any dispute arising from it is resolved by the courts of England and Wales, in each case unless the laws and/or courts of Scotland or Northern Ireland have been expressly selected by the Parties.
Unless the Parties have agreed alternative amendments which meet the requirements of Section 12, the provisions of Section 15 will apply.
No amendments to the Approved EU SCCs other than to meet the requirements of Section 12 may be made.
The following amendments to the Addendum EU SCCs (for the purpose of Section 12) are made:
a) References to the “Clauses” means this Addendum, incorporating the Addendum EU SCCs;
b) In Clause 2, delete the words:
“and, with respect to data transfers from Controllers to Processors and/or Processors to Processors, standard contractual clauses pursuant to Article 28(7) of Regulation (EU) 2016/679”;
c) Clause 6 (Description of the transfer(s)) is replaced with:
“The details of the transfers(s) and in particular the categories of Personal Data that are transferred and the purpose(s) for which they are transferred) are those specified in Annex I.B where UK Data Protection Laws apply to the data exporter’s Processing when making that transfer.”;
d) Clause 8.7(i) of Module 1 is replaced with:
“it is to a country benefitting from adequacy regulations pursuant to Section 17A of the UK GDPR that covers the onward transfer”;
e) Clause 8.8(i) of Modules 2 and 3 is replaced with:
“the onward transfer is to a country benefitting from adequacy regulations pursuant to Section 17A of the UK GDPR that covers the onward transfer;”
f) References to “Regulation (EU) 2016/679”, “Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the Processing of Personal Data and on the free movement of such data (General Data Protection Regulation)” and “that Regulation” are all replaced by “UK Data Protection Laws”. References to specific Article(s) of “Regulation (EU) 2016/679” are replaced with the equivalent Article or Section of UK Data Protection Laws;
g) References to Regulation (EU) 2018/1725 are removed;
h) References to the “European Union”, “Union”, “EU”, “EU Member State”, “Member State” and “EU or Member State” are all replaced with the “UK”;
i) The reference to “Clause 12(c)(i)” at Clause 10(b)(i) of Module one, is replaced with “Clause 11(c)(i)”;
j) Clause 13(a) and Part C of Annex I are not used;
k) The “competent supervisory authority” and “supervisory authority” are both replaced with the “Information Commissioner”;
l) In Clause 16(e), subsection (i) is replaced with:
“the Secretary of State makes regulations pursuant to Section 17A of the Data Protection Act 2018 that cover the transfer of Personal Data to which these clauses apply;”;
m) Clause 17 is replaced with:
“These Clauses are governed by the laws of England and Wales.”;
n) Clause 18 is replaced with:
“Any dispute arising from these Clauses shall be resolved by the courts of England and Wales. A Data Subject may also bring legal proceedings against the data exporter and/or data importer before the courts of any country in the UK. The Parties agree to submit themselves to the jurisdiction of such courts.”; and
o) The footnotes to the Approved EU SCCs do not form part of the Addendum, except for footnotes 8, 9, 10 and 11.
Amendments to this Addendum
The Parties may agree to change Clauses 17 and/or 18 of the Addendum EU SCCs to refer to the laws and/or courts of Scotland or Northern Ireland.
If the Parties wish to change the format of the information included in Part 1: Tables of the Approved Addendum, they may do so by agreeing to the change in writing, provided that the change does not reduce the Appropriate Safeguards.
From time to time, the ICO may issue a revised Approved Addendum which:
a) makes reasonable and proportionate changes to the Approved Addendum, including correcting errors in the Approved Addendum; and/or
b) reflects changes to UK Data Protection Laws;
The revised Approved Addendum will specify the start date from which the changes to the Approved Addendum are effective and whether the Parties need to review this Addendum including the Appendix Information. This Addendum is automatically amended as set out in the revised Approved Addendum from the start date specified.
If the ICO issues a revised Approved Addendum under Section 18, if any Party selected in Table 4 “Ending the Addendum when the Approved Addendum changes”, will as a direct result of the changes in the Approved Addendum have a substantial, disproportionate and demonstrable increase in:
a) its direct costs of performing its obligations under the Addendum; and/or
b) its risk under the Addendum,
and in either case it has first taken reasonable steps to reduce those costs or risks so that it is not substantial and disproportionate, then that Party may end this Addendum at the end of a reasonable notice period, by providing written notice for that period to the other Party before the start date of the revised Approved Addendum.
The Parties do not need the consent of any third party to make changes to this Addendum, but any changes must be made in accordance with its terms.
Alternative Part 2 Mandatory Clauses:
