INFORMATION SECURITY
Protecting Yourself and Your Business from Phishing Attacks

90% of cyber attacks start with a phishing email
The easiest and the most efficient way for hackers is to send phishing emails to users, asking them to take a specific course of action. Attackers pose as email and file sharing service providers, salespeople, job seekers, or even financial institutions. They ask the recipient to divulge valuable information or unknowingly assist in the installation of malware.
Security of the Esker on Demand platform
Recently, fraudsters have been sending emails to a handful of Esker on Demand (EoD) users, impersonating Esker to collect your EoD login information or to access your organization's data. These emails contain false information and may also refer to a call from an alleged Esker employee. These emails may ask you to click on a link to update your database or to review some documents after downloading them.
As a user, you have an active role to play in ensuring the security of your information. Being able to identify fraudulent activity is the first step in keeping sensitive information out of the hands of attackers. Did you receive a suspicious email? Are you having trouble logging in? Do you think you’ve been targeted in an attempted phishing attack?
If you received any of the following, chances are you have been targeted:
- an email containing a link to a non-authenticated copy of an EoD website
- an email asking for your EoD login information
- an email asking you to review documents by downloading them
- a call from an alleged Esker employee who does not know your customer or contract number, or who asks for your email address?
Protecting yourself from phishing scams
Indicators of phishing scams:
Check the sender email address
- Attackers often use domain names that are similar to or sound like authentic ones, such as 3sker.com or eskersupport.com.
- Authentic Esker-platform emails will always include @eskerondemand.com syntax. If this is not the case, the sender is not a legitimate EoD employee.
Check the email content
- Does the email suggest that you won something? Is there a sense of urgency or a threat? These methods make use of psychological tricks to force you take quick action without looking at the details too closely.
- Poor spelling and grammar mistakes can also be a clue. However, as attacks are getting more and more sophisticated, misspellings are becoming increasingly rare.
Check URLs and file attachments
- Trust your instincts: If something looks or feels wrong about the email, do not click on any links and do not open file attachments. Instead, hover the pointer over the link (but don't click on it!), to verify if the destination URL is, in fact, a legitimate one.
- Do not open or download any attachments if you're unsure. Contact the sender by phone or any other previously established method rather than replying to the email or using contact information from the suspicious email.
Check, verify, report:
In all cases, if you have any suspicion, please do not
- click any links
- open any attachments
- reply to any suspicious emails
- call any of the phone numbers listed in these emails
If you have received an email claiming to have been sent by the Esker platform and you are still unsure, contact the Esker Solution Support teams: https://www.esker.com/support-services/support/
If you clicked on a fraudulent URL, opened a malicious attachment, or entered any credentials, immediately change your EoD password and notify the IT/Security Team of your company.
How do I verify that I am on the legitimate Esker on Demand platform?
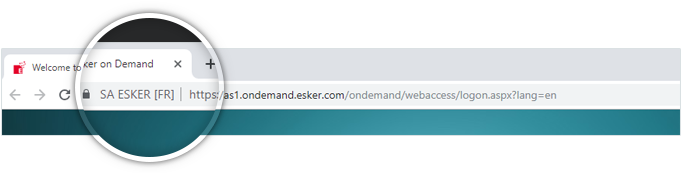
With Internet Explorer, Microsoft Edge, Google Chrome or Firefox
- The URL in the address bar must start with the syntax https:// (note the “s” after http)! This is possibly hidden in the address bar — double click to see the entire URL.
- A padlock icon must be present on the right or the left-hand-side of the URL.
Still not sure? Here is a list of the legitimate Esker platform URLs:
- https://as1.ondemand.esker.com/
- https://na2.esker.com/
- https://az3.ondemand.esker.com/
- https://we4.ondemand.esker.com/
- https://ae5.ondemand.esker.com/
- https://cc6.ondemand.esker.com/
- https://ne7.ondemand.esker.com
Our partners
- Coming Soon